KDS 2022 - Towards a Theory of Maximal Extractable Value I, CFMMs
A summary of results in this paper by Kulkarni, Diamandis & Chitra, which analyzes MEV in CFMMs.
1. Summary
The goal of the paper is to characterize the maximum value a MEV searcher using sandwich attacks can extract. Key results:
- Reordering MEV: Given order flow of user trades on a single CFMM, how much can reordering the trades affect excess price impact due to sandwich attacks? The ratio of the price impact of the worst case attack to average case attack is .
- Routing MEV: Given a network of CFMMs, how much do sandwich attackers affect the routing of trades? Network routing quality, measured by trade-weighted price impact, does not change much, asymptotically. The price of anarchy is , given sufficient liquidity.
Implicitly, many of these results have a connection to the privacy-utility tradeoff in CFMMs since searcher MEV profit can be mapped to a loss of user privacy.
2. Set-up and Definitions
2.1 Uniswap
We have reserves of token and reserves of token with token as the numeraire. A user’s trade of units of token for token is given by:
where is the pool percentage fee and is implicitly defined by this equality. The marginal price for a trade of size is is . The output number of tokens the user receives can be written in terms of the marginal price as:
Assume that , so that remains constant.
2.2 Slippage Limits
Since a user does not know the exact initial price at which their trade executes (other trades may execute first), they specify a slippage parameter . This Uniswap contract guarantees the user will receive no less than of the amount they would receive in the absence of other trades.
For example, consider a user who submits an trade of size and someone else submits a trade of size . A miner cannot execute a sequence of trades unless:
A user is responsible for setting , and so submits the trade pair . If the user sets too high, then it is possible this is a strict inequality. So, an MEV searcher can submit the trade such that:
The searcher worsens execution for the user by using up any slack in the user’s slippage parameter. The searcher can follow with another trade and profit. The triple is a sandwich attack. Combining the above equations, one can show that the MEV trade size is an increasing function of and 0 when .
2.3 CFMMs
The above set-up can be generalized to arbitrary CFMMs. A CFMM has reserves and a trading function . For any valid trade , the CFMM satisfies:
Here (positive sized trade) means the user wants to receive the asset means the user wants to send the asset to the contract.
For any positive-sized trade , the marginal price is:
The function is called the price impact function.
A CFMM is symmetrically -stable if it satisfies:
for and is symmetrically -liquid if it satisfies:
for . Both and are positive constants. Intuitively, this says the for bounded trade sizes, there is a linear upper bound on the price impact of buys and a linear lower bound on the price impact of sells.
Finally, one can show . The forward exchange function is given by , the amount of output token received for an input of .
3. Sandwich Attacks
The mechanics of the sandwich attack works as follows:
- Searcher seeing the user trade in the mempool, submits the trade which satisfies
- User trade goes through
- Searcher recoups initial investment by submitting trade . Assuming the searcher is risk neutral, they sell back all the output tokens they hold. We can convert back to units of the input token by implicitly solving the equation.
Keeping track of reserves over the course of these trades, we can see the final PNL in units of the input token is given by:
Intuitively, this makes sense. The user trades input tokens, but only gets back value worth input tokens. The searcher’s PNL is the difference. Notice if , then PNL is 0.
3.1 Bounds on Sandwich Attack Profitability
Assumptions:
- meets a smoothness conditions. There exist constants , such that for all :
- The price impact function grows sufficiently fast, ruling out constant sum market makers, for example where there is no price slippage.
Under these assumptions, it is possible to derive upper/lower bounds for , which depend on the liquidity, curvature and slippage factors. Combining these bounds with PNL formula, leads to the following result.
Result: Let . Then, for sufficiently large :
This implies that price impact and searcher PNL is linear in . It grows approximately at a rate.
3.2 Locality of Sandwich Profitability
Definition: Sandwich attacks for a sequence of trades are strongly local if for any ordered set where and , we have:
Strong locality says that it cannot be more profitable to sandwich bundles of trades versus bundling each trade individually. In this case, the problem simplifies since the searcher does not have to solve the Knapsack problem to find the most profitable subset of trades given blockspace limits.
4. Reordering MEV
Say there are a sequence of trades with default order . Further, we have a block size where (allowing the sandwicher to insert trades). Assume that for all .
The goal is to analyze, the cost of feudalism (CoF), which captures how much worse a user’s trade execution can be due to a permutation of the default trade order.
Definition: CoF is defined as:
The numerator describes the expected profit to MEV/miners from sandwiching the worse affected user, over all re-orderings of the trades. The denominator is for the average user.
The following result relies on the smoothness/curvature assumptions from the previous sections as well as the strong locality.
Result: If is strongly local, then .
The proof relies on upper bounding the numerator as and the denominator as . The result is fairly positive result on the impact of MEV as blockchains scale/grow, since it shows execution for the worst-case user only grows very slowly, logarithmically, in .
5. Routing MEV
Routing MEV for sandwich attacks describes excess value that sandwichers can extract from user trades over a full network of CFMMs. Here there is a concept of equilibrium routing, in which a user’s trade is routed from source to destination token in a CFMM network such that the price over all paths is equal. The excess price impact of sandwich attacks is the the social cost incurred by the network.
Two illustrative examples:
5.1 CFMM Pigou Example
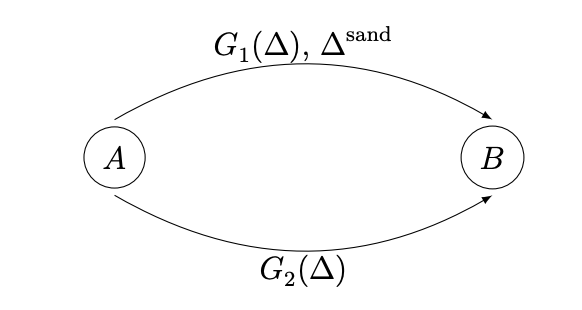 Say there are two Uniswap pools in the CFMM network that trade the same pair of assets, and . The initial reserves are equal .
Say there are two Uniswap pools in the CFMM network that trade the same pair of assets, and . The initial reserves are equal .
In equilbrium, a user who wants to trade units of for , will split the trade such that the price over both paths is equal. For the price impact function and , we will have where , is the fraction of trades made in pool 1. Specifically, is the solution to:
Note that ends up being concave, so solving , gives the equalibrium condition. In the equal reserves case, this works out to .
Now if there is a sandwich attacker on pool 1 and the user submits a slippage parameter . The optimum changes to:
This comes from directly using the optimal MEV sandwich equation. As expected, for , the equilbrium . The user moves away from pool 1, since the sandwicher makes it more expensive to trade there. The larger the , the closer is to 0 and the smaller the optimum .
5.2 CFMM Braess Example
A somewhat counterintutive example here shows that the presence of sandwich attacks improves network flow and the MEV profit is bounded. So, while a single user may experience worse execution, the aggregate social welfare improves.
Three cases:
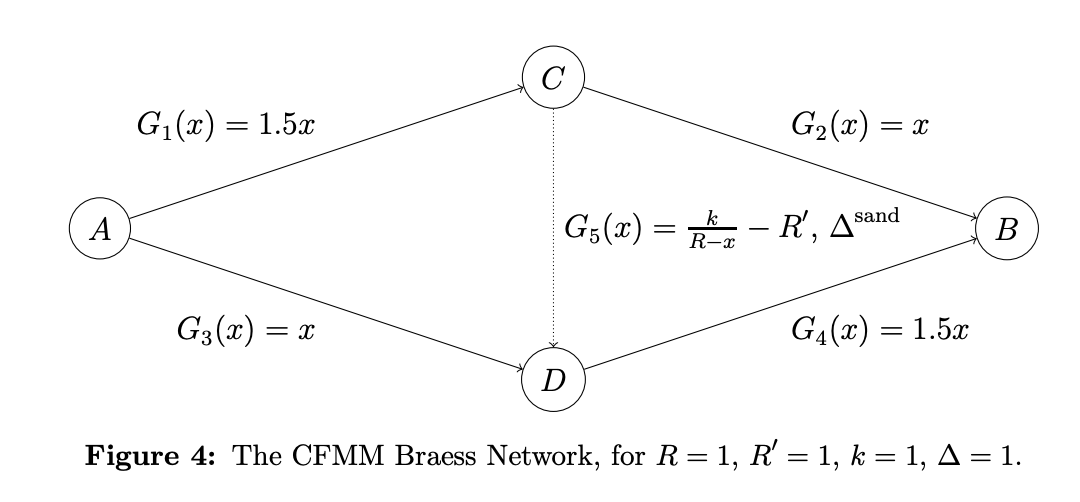
- Case 1: There is no CFMM for the pair , so . Since both paths, and , cost the same, the fraction of a trade allocated to both is . The net output of token is:
- Case 2: There is now a CFMM for the pair , so . Using a symmetry of the price paths, you can get to the output formula below and the equilibrium . Interestingly, you see that the user’s net output reduces in this case:
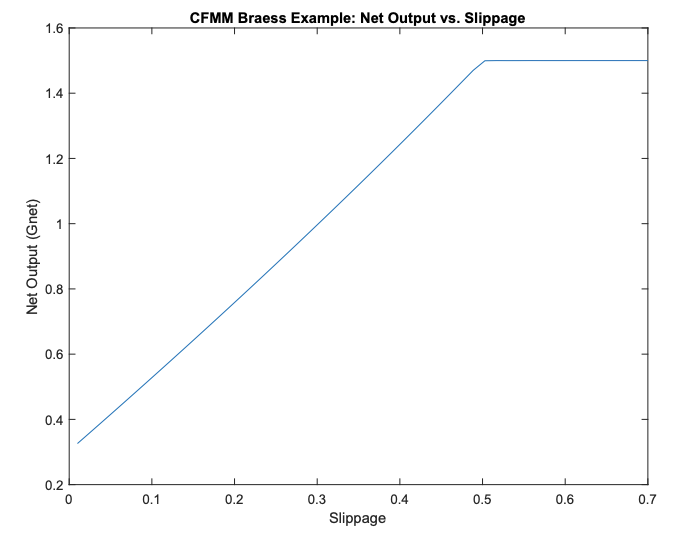
- Case 3: Add a sandwicher on the path and the user now adds a slippage limit for the path . Again, the equilbrium, shifts much like the CFMM Pigou Example and depends on . But, here we actually see that as increases, the user moves away from taking the middle path and increases output. This continues the equilibrium converges to case 1, . The presence of the sandwicher forces users to effectively re-allocate across the network to avoid congestion.
5.3 Price of Anarchy
5.3.1 Network Set-up
The theoretical results depend on the following set-up: There is a graph where each vertex is a token and each edge is a CFMM for a pair of assets. For each edge there is an associated price and forward exchange function, and . Each trade is specified as for a trade of from vertex to with a slippage parameter of .
5.3.2 Equilibrium Splitting
For a trade , denote the set of all paths from to as . Let be the splitting vector that denotes the fraction of routed over all the possible paths.
Definition: A splitting vector is an equilibrium splitting in price, if for all , when , we have:
for all other .
The implication here is that for all paths on which there is non-zero traffic in equilibrium, the user must face the same price. This is analagous to the equilbrium from the CFMM Pigou Example.
5.3.3 Sandwich Attacks
Much like the for the proof of the PNL bounds for the sandwich attacks, it is possible to upper/lower bound the searcher’s trade size for each edge in the network in terms of the cumulative trade through , . It is a bit more complicated here because the user only provides a single slippage parameter , so the searcher has to back out the implied slippage for each individual edge in a path .
5.3.4 Social Cost and Price of Anarchy (PoA)
To define the social cost, we first define the cost of each edge in terms of the sandwich size . The cost for a given edge is:
where is the price of the output token for edge in terms of the infinitely liquid numeraire, like USD. Here, represents the excess price impact due to the sandwich attack in units of USD per input token.
Definition: The aggregate cost of sandwiching on the network is given by a trade-weighted average:
Definition: PoA is defined as following. Let be any equilbrium splitting. Then:
This reflects the ratio of the equilbrium social cost to the minimizer.
The final result of the paper shows the is upper bounded by a constant, that depends on the curvature/slippage parameters of the network.
Result: There exists a function that is constant in the size of the network graph such that:
where is the set of liquidity, slippage and curvature parameters of the underlying CFMMs.
The result is similar to the Braess example, show that asymptotically, the presence of sandwichers, does not lead to worse aggregate network price impact.